aircrack-ng套件介绍
只要学习无线安全,Aircrack-ng套件就是需要接触的内容,其包含20多种专门用于审核wifi网络的攻击,并且都是命令行,我今天只会简要记录几个常用工具
Airmon-ng(快捷监控)
这个工具能快速将网卡调整至监听状态,并且和iw一样可以选择信道
在此基础上它还存在参数check能检查当前环境是否存在干扰进程,我们在工作的时候可以利用它将这些进程暂时击溃防止干扰
┌──(root㉿kali)-[/home/wackymaker/test]
└─# airmon-ng start wlan0
Found 2 processes that could cause trouble.
Kill them using 'airmon-ng check kill' before putting
the card in monitor mode, they will interfere by changing channels
and sometimes putting the interface back in managed mode
PID Name
860 NetworkManager
2855 wpa_supplicant
PHY Interface Driver Chipset
phy1 wlan0 mt7921u MediaTek Inc. Wireless_Device
(mac80211 monitor mode vif enabled for [phy1]wlan0 on [phy1]wlan0mon)
(mac80211 station mode vif disabled for [phy1]wlan0)
┌──(root㉿kali)-[/home/wackymaker/test]
└─# iwconfig
lo no wireless extensions.
eth0 no wireless extensions.
wlan0mon IEEE 802.11 Mode:Monitor Frequency:2.457 GHz
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:on
可以看到由airmon启动的监听模式还会给我们换一个名字,这是正常的airmon防止我们识别失误,会启动虚拟网卡,并且这里可以看到有两个进程会干扰我们的工作
也可以使用check来详细输出
┌──(root㉿kali)-[/home/wackymaker/test]
└─# airmon-ng check
Found 2 processes that could cause trouble.
Kill them using 'airmon-ng check kill' before putting
the card in monitor mode, they will interfere by changing channels
and sometimes putting the interface back in managed mode
PID Name
860 NetworkManager
2855 wpa_supplicant
可以快捷的kill掉干扰进程
┌──(root㉿kali)-[/home/wackymaker/test]
└─# airmon-ng check kill
Killing these processes:
PID Name
2855 wpa_supplicant
取消监听
┌──(root㉿kali)-[/home/wackymaker/test]
└─# airmon-ng stop wlan0mon
PHY Interface Driver Chipset
phy1 wlan0mon mt7921u MediaTek Inc. Wireless_Device
(mac80211 station mode vif enabled on [phy1]wlan0)
(mac80211 monitor mode vif disabled for [phy1]wlan0mon)
指定监听信道,直接给数字就行了,非常迅速
┌──(root㉿kali)-[/home/wackymaker/test]
└─# airmon-ng start wlan0 11
PHY Interface Driver Chipset
phy1 wlan0 mt7921u MediaTek Inc. Wireless_Device
(mac80211 monitor mode vif enabled for [phy1]wlan0 on [phy1]wlan0mon)
(mac80211 station mode vif disabled for [phy1]wlan0)
┌──(root㉿kali)-[/home/wackymaker/test]
Airodump-ng(数据包捕获)
Airodump-ng专门用于数据包捕获,并且也是之后破解wpa1和wpa2wifi密码的重要依据
其正常显示参数如下
| Field | Description |
|---|---|
| BSSID | Shows the MAC address of the access points. (显示接入点的 MAC 地址) |
| PWR | Shows the “power” of the network. The higher the number, the better the signal strength. (显示网络的“力量”。数字越高,信号强度越好。) |
| Beacons | Shows the number of announcement packets sent by the network. (显示网络发送的公告数据包数。) |
| #Data | Shows the number of captured data packets. (显示捕获的数据包数。) |
| #/s | Shows the number of data packets captured in the past ten seconds. (显示过去十秒内捕获的数据包数。) |
| CH | Shows the “Channel” the network runs on. (显示网络运行的“通道”。) |
| MB | Shows the maximum speed supported by the network. (显示网络支持的最大速度。) |
| ENC | Shows the encryption method used by the network. (显示网络使用的加密方法。) |
| CIPHER | Shows the cipher used by the network. (显示网络使用的密码。) |
| AUTH | Shows the authentication used by the network. (显示网络使用的身份验证。) |
| ESSID | Shows the name of the network. (显示网络的名称。) |
| STATION | Shows the MAC address of the client connected to the network. (显示连接到网络的客户端的 MAC 地址。) |
| RATE | Shows the data transfer rate between the client and the access point. (显示客户端和接入点之间的数据传输速率。) |
| LOST | Shows the number of data packets lost. (显示丢失的数据包数。) |
| Packets | Shows the number of data packets sent by the client. (显示客户端发送的数据包数。) |
| Notes | Shows additional information about the client, such as captured EAPOL or PMKID. (显示有关客户端的其他信息,例如捕获的 EAPOL 或 PMKID。) |
| PROBES | Shows the list of networks the client is probing for. (显示客户端正在探测的网络列表。) |
由于隐私问题不好处理,我建议看我博客的兄弟们接下里使用自己的网卡测试,之后我将只输出命令
输出截获所有数据情况
sudo airodump-ng wlan0mon
可选过滤参数
--bssid 34:29:12:A6:BA:48 #由mac地址筛选ap
--channel 或者 -c $number #由信道筛选ap
--essid "wifi名称" #由wifi名称筛选ap
一般都是要过滤的,要不然看不清输出
默认情况下,airodump-ng 配置为专门扫描在 2.4 GHz 频段上运行的网络。不过,如果无线适配器与 5 GHz 频段兼容,我们可以指示 airodump-ng 利用 –band 选项在其扫描中包含此频率范围。我们可以在此处找到可用于 Wi-Fi 的所有 WLAN 信道和频段的列表。
sudo airodump-ng wlan0mon --band a
a代表5g,b代表11兆限速的2.4g,g代表54兆限速的2.4g
所以想筛选全也可以
sudo airodump-ng wlan0mon --band abg
如果需要导出文件的话
airodump-ng wlan0mon --write wackymaker
会在当前目录生成
wackymaker-01.cap
wackymaker-01.csv
wackymaker.kismet.csv
wackymaker.kismet.netxml
wackymaker.log.csv
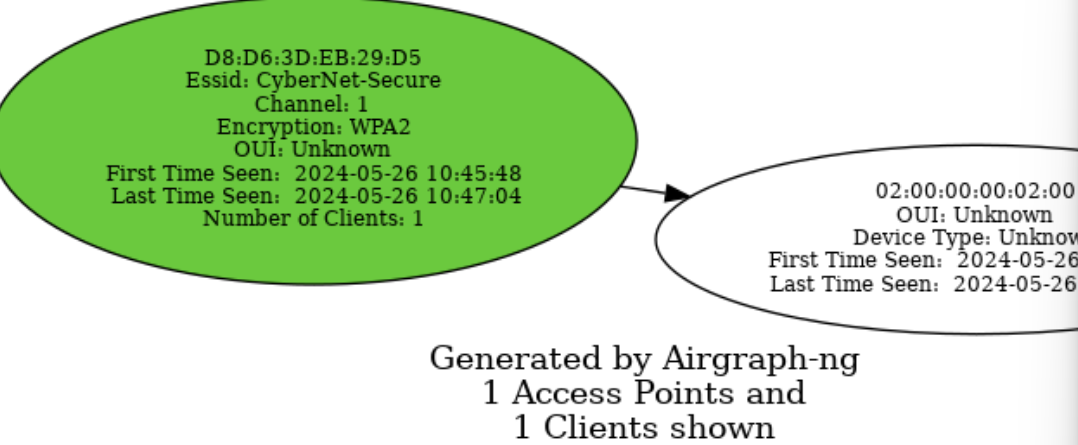
Airgraph-ng(无线拓扑图)
当我们用Airodump-ng抓下来csv后就可以利用Airgraph-ng生成拓扑图,不好用,但是聊胜于无吧,简单记下命令
生成客户端与ap关系图CAPR,生成的图片会可视化当前的ap和客户端连接情况
sudo airgraph-ng -i wacky-01.csv -g CAPR -o CAPR.png
类似如下效果
还可以生成通用探针图CPG生成的图片会可视化当前ap和所有客户端的联系,包括并没有接入或者准备接入网络的客户端
sudo airgraph-ng -i wacky-01.csv -g CPG -o CAPR.png

Aireplay-ng(数据包注入)
我会在后续的学习中具体的讲述它的使用,它是比较重要的一个攻击模块,用于发送数据包攻击
只记两条命令
测试当前网卡是否允许注入
sudo aireplay-ng --test wlan0mon
看到回显
Injection is working!
即可
洪水攻击(取消身份验证攻击)
sudo aireplay-ng -0 5 -a 00:14:6C:7A:41:81 -c 00:0F:B5:32:31:31 wlan0mon
-0 表示取消身份验证
5 是要发送的 deauth 次数(如果您愿意,可以发送多个);0 表示连续发送它们
-a 00:14:6C:7A:41:81 是接入点的 MAC 地址
-c 00:0F:B5:32:31:31 是要取消身份验证的客户端的 MAC 地址;如果省略,则连接的所有客户端都会被攻击
Airdecap-ng(解密无线流量)
当我们抓取wifi流量包后会发现抓取协议都是802.11
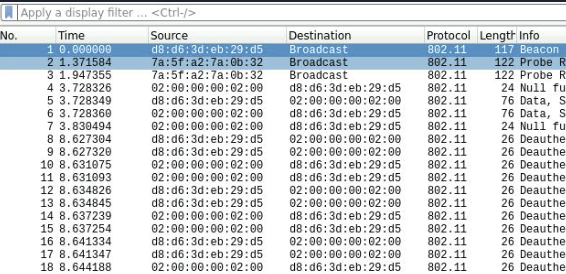
如果想要解密的话,我们需要拥有wifi密钥
未加密数据包可以直接解密
sudo airdecap-ng -b 00:14:6C:7A:41:81 opencapture.cap
Total number of stations seen 0
Total number of packets read 251
Total number of WEP data packets 0
Total number of WPA data packets 0
Number of plaintext data packets 0
Number of decrypted WEP packets 0
Number of corrupted WEP packets 0
Number of decrypted WPA packets 0
Number of bad TKIP (WPA) packets 0
Number of bad CCMP (WPA) packets 0
wep加密需要wep密钥
sudo airdecap-ng -w 1234567890ABCDEF wack-01.cap
Total number of stations seen 6
Total number of packets read 356
Total number of WEP data packets 235
Total number of WPA data packets 121
Number of plaintext data packets 0
Number of decrypted WEP packets 0
Number of corrupted WEP packets 0
Number of decrypted WPA packets 235
Number of bad TKIP (WPA) packets 0
Number of bad CCMP (WPA) packets 0
wpa加密需要wifi密码和wifi的essid
sudo airdecap-ng -p 'abdefg' wack-01.cap -e "Wireless"
Total number of stations seen 6
Total number of packets read 356
Total number of WEP data packets 235
Total number of WPA data packets 121
Number of plaintext data packets 0
Number of decrypted WEP packets 0
Number of corrupted WEP packets 0
Number of decrypted WPA packets 121
Number of bad TKIP (WPA) packets 0
Number of bad CCMP (WPA) packets 0
解密后流量就是正常的
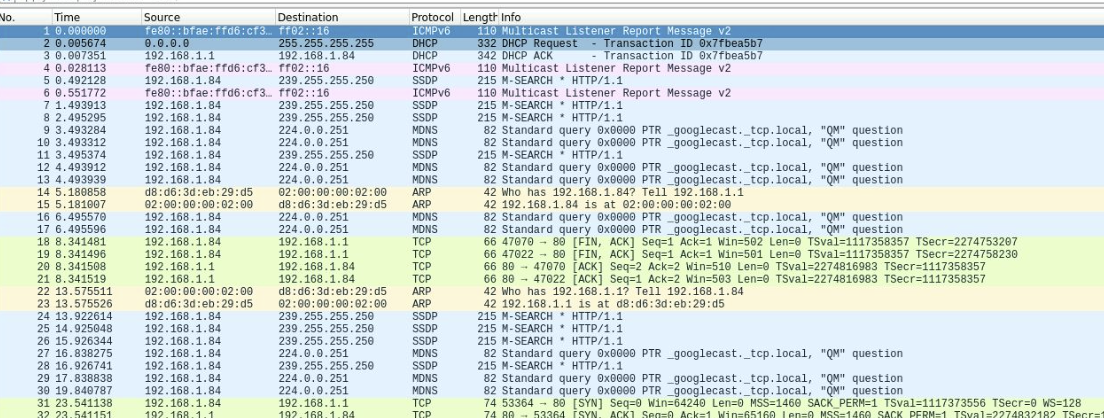
总结
还有一个用于破解密钥的,但是暂不记录,后续破解wifi密码模块会详细说明